I will explain the “how can we integrate the openshift with nexus for image registry” today. For this topic we need the nexus and openshift cluster. And we are accessing the nexus repository with nginx reverse-proxy.
Step1:
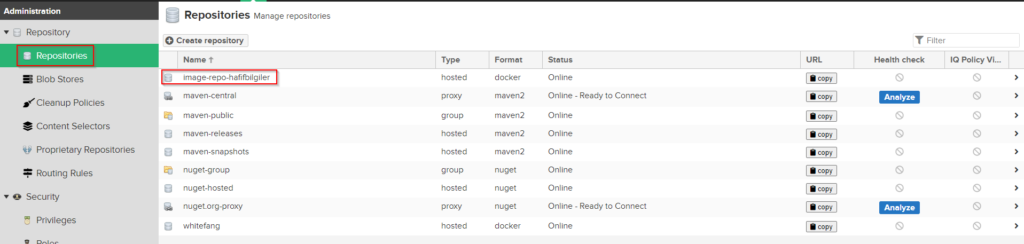
Create new repository on Nexus Application.

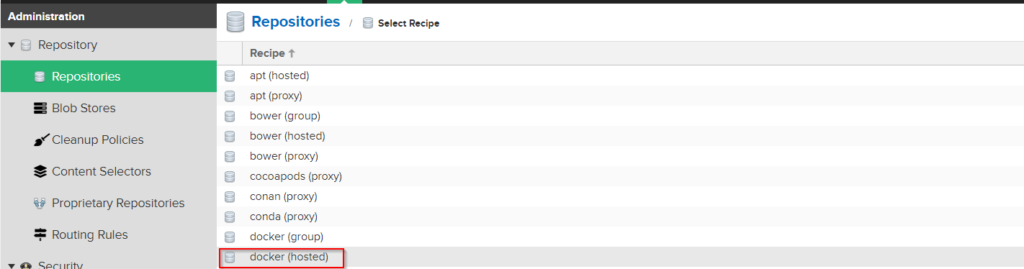
After above section click the http checkbox and write your port number in the port field. I have been choosen the “9090” port number.
Check your repository name from repository list.
Step2:
Create new server block in the nginx configuration file(i am using the nginx for reverse proxy with secure connection.)
vim /etc/nginx/conf.d/default.confserver {
listen 8443 ssl; #Port number which i will use for https protocol
server_name nexus.192.168.56.102.nip.io; # My Nexus Server Name
ssl_certificate /opt/tls_repo_crt.crt;
ssl_certificate_key /opt/tls_repo_key.key;
client_max_body_size 640M;
location / {
proxy_pass http://nexus.192.168.56.102.nip.io:9090;
}
}Then restart the nginx to read new configuration.
systemctl restart nginxThen check your repository with login.

Step3:
Create the new new secret to using in the resource file. When some resource creating openshift will use the this secret to login the external image repository.
Note:
Your cluster have to access the your nexus machine and releated repository port number.
oc create secret docker-registry openshift-image-registry --docker-server=nexus.192.168.56.102.nip.io:8443 --docker-
username=<your nexus user name> --docker-password=<your nexus password> --docker-email=openshift@hafifbilgiler.comStep4:
Create new configmap to register the ca certificate for openshift. If you don’t create this configmap you will get the error from your resources logs like below.
Copy your ca certifcate on your openshift bastion server or controller machine. Then run command below to create configmap.
"x509: certificate signed by unknown authority"oc create configmap registry-docker-repo -n openshift-config --from-file=nexus.192.168.56.102.nip.io..8443=/opt/certicate.caNOTE:
When you need the other repository to add your cluster you must edit above configmap and add the new ca certificate file for other dns name and port number.
Step5 :
Add new tag the nginx image with new repository name and push your image for newly created repository.
docker login nexus.192.168.56.102.nip.io:8443
docker tag nginx:latest nexus.192.168.56.102.nip.io:8443/default/nginx:latest
docker push nexus.192.168.56.102.nip.io:8443/default/nginx:latest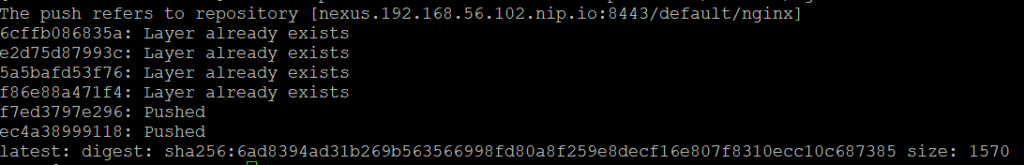

Step6:
Create new deployment file and use the new image with pull secret.
vim test.yamlapiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deployment
namespace: default
labels:
app: nginx
spec:
replicas: 3
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
imagePullSecrets:
- name: openshift-image-registry
containers:
- name: nginx
image: nexus.192.168.56.102.nip.io:8443/default/nginx:latest
ports:
- containerPort: 80kubectl apply -f test.yamlThat’s it. Have happy works.